
Setting the name to a specific string of characters revealed remote server details

Security researchers investigating the recently discovered and “extremely bad” Log4Shell exploit claim to have used it on devices as varied as iPhones and Tesla cars. Per screenshots shared online, changing the device name of an iPhone or Tesla to a special exploit string was enough to trigger a ping from Apple or Tesla servers, indicating that the server at the other end was vulnerable to Log4Shell.
In the demonstrations, researchers switched the device names to be a string of characters that would send servers to a testing URL, exploiting the behavior enabled by the vulnerability. After the name was changed, incoming traffic showed URL requests from IP addresses belonging to Apple and, in the case of Tesla, China Unicom — the company’s mobile service partner for the Chinese market. In short, the researchers tricked Apple and Tesla servers into visiting a URL of their choice.
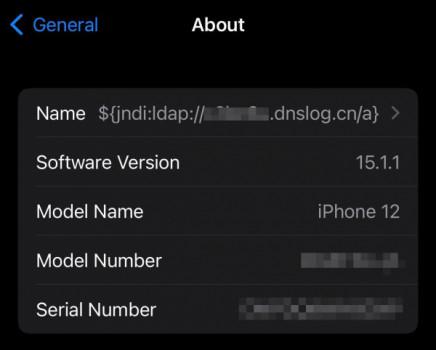
The iPhone demonstration came from a Dutch security researcher; the other was uploaded to the anonymous Log4jAttackSurface Github repository.
Assuming the images are genuine, they show behavior — remote resource loading — that should not be possible with text contained in a device name. This proof of concept has led to widespread reporting that Apple and Tesla are vulnerable to the exploit.
While the demonstration is alarming, it’s not clear how useful it would be for cybercriminals. In theory, an attacker could host malicious code at the target URL in order to infect vulnerable servers, but a well-maintained network could prevent such an attack at the network level. More broadly, there’s no indication that the method could lead to any broader compromise of Apple or Tesla’s systems. (Neither company responded to an email request for comment by time of publication.)
Log4Shell is all the more serious for being relatively easy to exploit
Still, it’s a reminder of the complex nature of technological systems, which almost always depend on code pulled in from third-party libraries. The Log4Shell exploit affects an open-source Java tool called log4j which is widely used for application event logging; though it’s still not known exactly how many devices are affected, but researchers estimate that it is in the millions, including obscure systems that are rarely targeted by attacks of this nature.
The full extent of exploitation in the wild is unknown, but in a blog post, digital forensics platform Cado reported detecting servers trying to use this method to install Mirai botnet code.
Log4Shell is all the more serious for being relatively easy to exploit. The vulnerability works by tricking the application into interpreting a piece of text as a link to a remote resource, and trying to retrieve that resource instead of saving the text as it is written. All that’s necessary is for a vulnerable device to save the special string of characters in its application logs.
This creates the potential for vulnerability in many systems that accept user input, since message text can be stored in the logs. The log4j vulnerability was first spotted in Minecraft servers, which attackers could compromise using chat messages; and systems that send and receive other message formats like SMS clearly are also susceptible.
At least one major SMS provider appears to be vulnerable to the exploit, according to testing conducted by The Kupon4U. When sent to numbers operated by the SMS provider, text messages containing exploit code triggered a response from the company’s servers that revealed information about the IP address and host name, suggesting that the servers could be tricked into executing malicious code. Calls and emails to the affected company had not been answered at time of publication.
An update to the log4j library has been released to mitigate against the vulnerability, but patching of all vulnerable machines will take time given the challenges of updating enterprise software at scale.








